Understanding Exploit Development
Exploit development is the art and science of discovering vulnerabilities in systems and crafting methods to exploit them. Here, we explore the various stages involved in developing exploits:
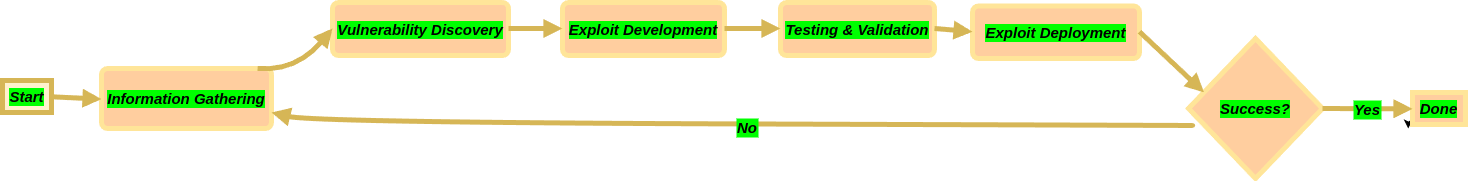
- Surveillance and Information Gathering
- Source Code Analysis: Examining open-source projects and binaries to understand potential weaknesses.
- Protocol Analysis: Studying communication protocols to identify security flaws.
- Reverse Engineering
- Disassembling Software: Using tools like IDA Pro or Ghidra to deconstruct binaries and understand their functionality.
- Dynamic Analysis: Running software in controlled environments to observe behavior and identify vulnerabilities.
- Identifying Vulnerabilities
- Common Weaknesses: Buffer overflows, RCE, DOS, and other improper authentication mechanisms.
- Zero-Day Exploits: Discovering and leveraging unknown vulnerabilities before they are patched.
- Developing Exploits
- Proof of Concept: Crafting and demonstrating exploits to validate the presence of vulnerabilities.
- Payload Delivery: Techniques for delivering payloads, from network exploitation to social engineering.
Vulnerability Analysis
Vulnerability analysis is a crucial aspect of cybersecurity, focusing on identifying and mitigating weaknesses before they can be exploited:
- Static Analysis: Reviewing source code and binaries for known vulnerability patterns.
- Dynamic Analysis: Monitoring software behavior during execution to detect anomalies.
- Penetration Testing: Simulating attacks to identify and rectify security flaws.
- Security Audits: Comprehensive assessments of software and hardware to ensure robustness.
A Word of Caution
While this blog outlines the process of developing and deploying exploits, it’s essential to remember that these activities should only be conducted in a legal and ethical manner. Unauthorized access to systems is illegal and can have severe consequences. Always ensure you have permission before testing or exploiting any system.
Warning: This content is for educational purposes only. The author is not responsible for any damage caused by the misuse of the information provided. Users bear sole responsibility for their actions.






