Exploit Dev # 9 : Remote Exploitation of SNMP Configuration in PLC – Vulnerability @ Hack-the-Box
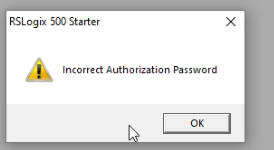
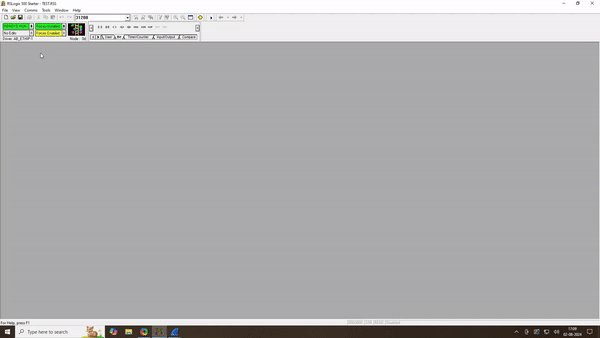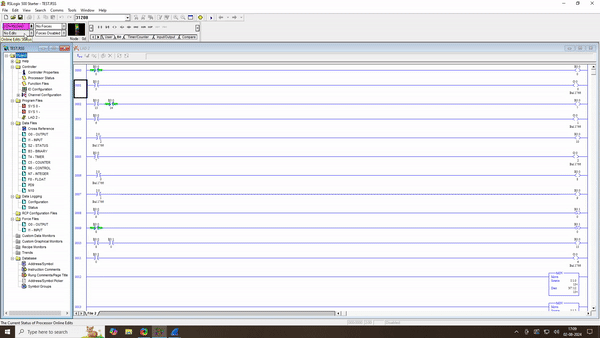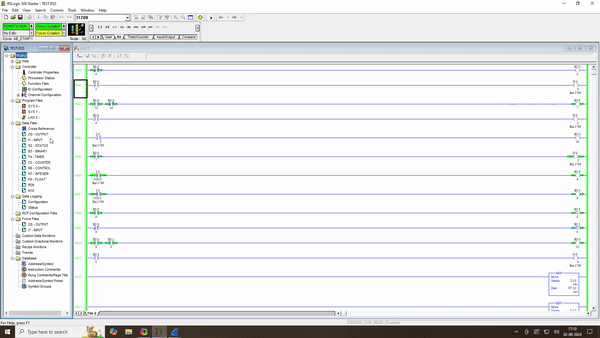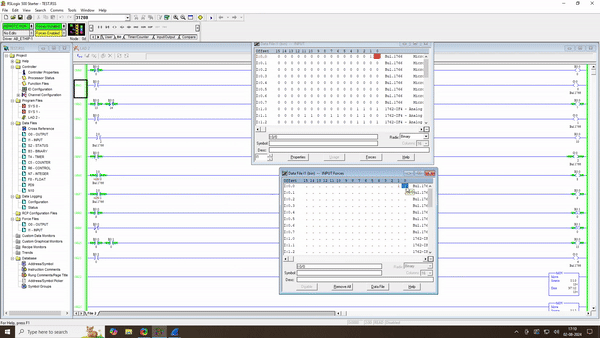
In Exploit Development # 9 : Remote Exploitation of SNMP Configuration , we’re tackling a significant vulnerability in the Allen Bradley Micrologix 1400 Series B. This time, our focus is on the ability to remotely enable or disable the SNMP (Simple Network Management Protocol) feature. Our exploit involves sending specially crafted packets to manipulate SNMP […]